
Tea App Breach: What Happened and Why It Matters for Your Privacy
Categories: Cybersecurity, Data, Data Breach, Data Privacy, Digital Footprint, Encryption, Privacy Guides, Social Media, Social Media Management, Surveillance
The recently viral Tea app has recklessly mishandled user data, endangering many of the women it claimed to protect.
Tea is an app that gained fast popularity as a safety tool for women navigating dating. It allows users to anonymously share reviews and warnings about men they’ve dated or matched with. The concept is rooted in community protection. Users can post a man’s name, location, photo, and personal experiences, and others can comment or flag the post. To join, women are asked to verify their identity with a selfie and sometimes their ID to confirm they’re not impersonating someone.
With over two million sign-up requests and topping the App Store charts, Tea’s success was rapid. But so was the fallout.
What Was Breached
In July 2025, Tea suffered a serious data breach. A vulnerability in one of their data storage systems exposed over 72,000 images. This included around 13,000 sensitive files like selfies and photo IDs that users submitted for verification, as well as 59,000 images from inside the app itself — including private direct messages and anonymous posts.
These files were accessed without authentication and shared publicly on 4chan, a forum notorious for hosting leaked and sensitive content. Screenshots from the breach showed people rifling through users’ faces, licenses, and conversations, turning a platform built around safety into a source of exposure.
This is a clear example of sensitive personal information being recklessly mishandled by a company that framed itself as a safety measure for women. Instead, it’s has created a near irreversible vulnerability for many of the women that used it.
Why This Is a Big Deal
Even though Tea claimed the exposed data was from more than two years ago, the harm is current and very real. Many of these users submitted government-issued IDs and selfies – which are now publicly accessible. That opens the door to identity theft, harassment, blackmail, or being doxxed.
The damage isn’t limited to digital spaces. A user’s face and legal name paired with their location and dating history can create serious offline safety risks. What was meant to be a protective space has, for many, become a vulnerability.
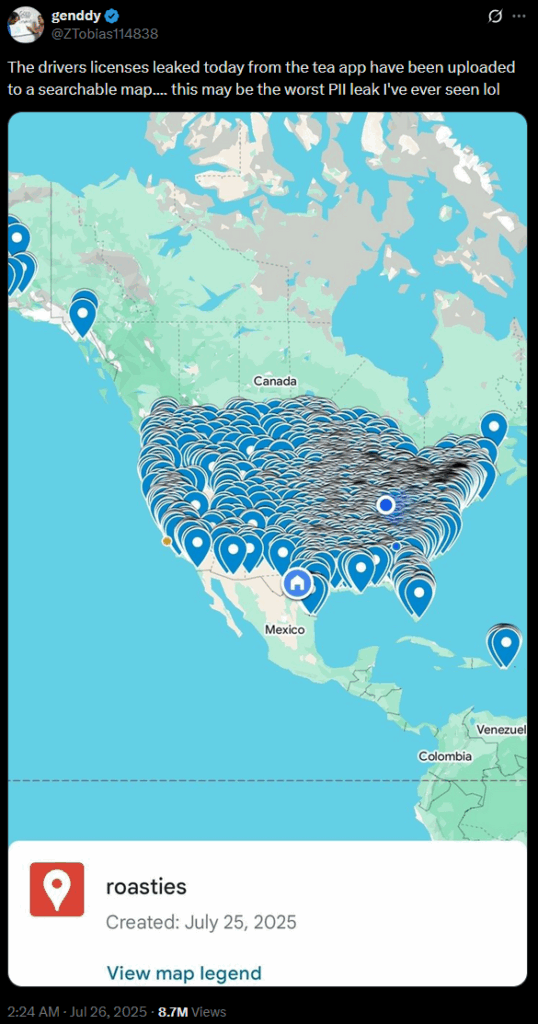
A twitter user has claimed that all the exposed drivers licenses have now been uploaded to a searchable map. The user did not share a link to this map, and nor will we.
Who Uses Tea, and Why They Were Targeted
Tea was created for women who wanted to share honest stories about their dating experiences and learn more about the people they meet online. Its appeal was grounded in trust, community, and anonymity. The verification process was meant to keep that community safe — not expose people.
But that same data made it a tempting target. Personal photos, legal documents, and candid commentary all in one place? Without proper protections, that kind of data is a goldmine for trolls and bad actors.
What This Teaches Us About Personal Info Online
This breach is a reminder that no app is immune to mistakes, especially when sensitive data is involved.
Even platforms created with safety in mind can put users at risk if their backend systems are not secure or updated. Just because an app goes viral does not mean it is secure.
Simply put – it’s not good enough to just be pro-safety; you need to build your product with protection ingrained in its foundation.
At Redact, we don’t store any customer data other than the email address you use to access your account. If we’re ever breached – our customer’s sensitive data is inherently protected – because we don’t have it.
People should think carefully about where they upload their personal info. Always ask:
- What am I sharing?
- Who stores it? How do they store it?
- Is there a way to delete it?
- Do I trust them to protect it?
When an app requires personal documentation like a driver’s license, that creates long-term risk if the system is ever breached – and means keeping it secure is even more essential.
How to Remove Your Data from the Tea app
Removing your data from the Tea app should be a straightforward, easy process. There’s likely a growing backlog of takedown requests – you should submit yours urgently to ensure it’s processed as quickly as possible. Here’s how you do it, according to Tea;
For takedown requests, email support@teaforwomen.com with your name, city/state, as much information as possible about the content in question, and a photo of yourself (to help us locate the content)
If you don’t have data on Tea, or aren’t aware of any – email them with only the essential information. After the recent breach, you can’t trust Tea to handle email takedown requests responsibly. However, you should still endeavor to have them remove any information they have about you.
Once you’ve requested Tea remove your data – you should start thinking about your broader digital footprint, and the potential risks it creates. This includes any information about you online – public listings, social media profiles, posts, comments, and even messages.
In the event of inevitable future breaches, minimizing your digital footprint is the best way to mitigate harm.
How to Take Control of Your Data
One of the best steps anyone can take is reviewing and reducing what’s already out there – this can take days or longer depending on how heavily you use the internet, particularly social media. That’s where tools like Redact can help.
Redact allows you to bulk-delete old posts, comments, likes, messages, and more across dozens of major platforms. That includes:
- Facebook (posts, likes, comments, messages)
- Twitter (tweets, retweets, likes, replies, messages)
- Reddit (posts, comments, upvotes)
- Discord (messages across servers and DMs)
- LinkedIn (likes, posts, comments, job history)
- Tumblr, GitHub, Pinterest, Stack Exchange, and more
You can filter by keyword, platform, or time range, preview everything before deletion, and even schedule regular cleanups so your history stays managed over time.
You can’t undo a breach that already happened, but you can reduce your digital footprint and prevent future exposure. In a world where platforms rise and fall overnight, it pays to stay cautious, selective, and in control.