
Social Engineering Threats on Twitter
Categories: Cybersecurity, Data, Data Privacy, Digital Footprint, Privacy Guides, Promotion, Redact Features, Social Media, Social Media Management, Twitter
Twitter’s speed, public nature, and searchability make it a perfect environment for scammers and social engineers. With millions of conversations happening every day, it only takes one post to make you a target.
Back in 2020, hackers gained access to Twitter’s internal systems by social engineering targeting Twitter staff. The hackers then gained access to Twitter accounts belonging to some of the world’s most prominent figures; Joe Biden, Jeff Bezos, Elon Musk, Barack Obama, and more. They used the profiles to conduct a massive bitcoin scam, requesting people send the wallet $1,000 to “double their money”
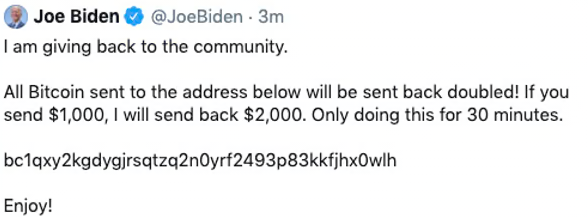
This began with social engineering access to Twitter systems, to compromise and leverage Twitter profiles with massive reach and with trusting audiences. Since 2020, AI has seen widespread adoption by hackers. As a result, this type of attack is no longer reserved for public figures and the ultra-wealthy. Something as simple as your identity is enough of a reason for threat actors to target you for a social engineering attack.
Impersonation Scams Are Everywhere
To add fuel to the fire, recent feature developments on Twitter / X have made it far easier to impersonate public figures on Twitter – it’s become one of the most common attack methods on Twitter.
When paid verification accounts were introduced on Twitter, an impersonator account posing as the pharmaceutical company Eli Lilly tweeted that “insulin is now free.” The false claim led to a sharp drop in the company’s stock value.
Scammers create fake accounts that look like real companies, influencers, or support teams. If you tweet a complaint to your bank, phone provider, or airline, a fraudulent “support” account might quickly respond offering help. These accounts often send links that look legitimate but lead to phishing sites aimed at stealing your passwords or personal data.
Further, tweeting a complaint to your bank publicly identifies you as a customer of that bank. Don’t do that.
Reconnaissance and Oversharing
Social engineers don’t just rely on phishing, they use Twitter to gather information passively. Your tweets, replies, likes, and profile bio can reveal a lot about you.
Attackers can uncover:
- Your workplace and job title
- Events you have attended
- Travel plans or check-ins
- Relationships, friend groups, or coworkers
- Personal trivia like pet names or schools
- Photos with geotags or identifiable landmarks
- Companies, software, or platforms that you are a member of
All of this information can be used by a threat actor to build a detailed profile of you. This can be leveraged as a tool to impersonate you and scam your friends or family, bypass your account security questions, or guess your passwords.
Small Tweets, Big Risks
Even tweets from years ago can be dangerous – a nostalgic post about your first car or a sibling’s birthday might seem harmless. Or they might be answers to security questions.
A pic of your cat with the caption “taking fluffy to the vet, wish us the best!” can easily become a convincing phone-call to your coworker to have them share a 2-factor authentication code because you’re “at the vet without your laptop”.
The risk factor on Twitter / X is directly tied to how much content you have on there. That risk factor is multiplied for every social media platform you have, and the volume of content on each of them. The best thing you can to to stay safe is get your digital footprint under control – simply by reducing how big it is.
How To Prevent Social Engineering Attacks
Fully preventing social engineering attempts is impossible – they could be directly targeted at you, or you might be targeted through your friends or family. For this reason – you should always remain vigilant, and a little skeptical.
We also recommend having a conversation about social engineering with people close to you, so they understand the risks and how to reduce the damage a social engineering attack could do.
However, the likelihood that you become a proxy for a social engineering attack is directly related to the volume of public info is out there about you. For most people, this boils down to social media – posts, comments, profiles, and other activity. If you want to keep yourself safe, you should:
- Set 2-factor authentication up on all platforms. This dramatically reduces the likelihood someone could access your account, and leverage the private data inside it to harm you or people close to you.
- Private your accounts. This limits the volume of information that hackers can easily access about you, without compromising your account directly.
- Audit and remove public content with sensitive info. Go through each of your accounts (public and private) and remove any content that contains personal information – names, locations, pet names, workplaces, even your regular cafe.
- Audit and remove private content with sensitive info. In the event of a hack, you want to minimize the amount of harm that the hacker can do. This means clearing our old messages with your friends and family, especially if it contains any personal information that could be leveraged in an attack.
You might be thinking the “audit and removal” process for socials and messaging services is going to be painful and time-consuming. Unfortunately, most platforms rely on ad revenue generated by weaving ads throughout your content. As a result, they don’t make it easy to clean up your old content.
For most platforms, you’ll need to manually sort through and delete each individual message, post or comment. That’s why we built Redact.dev.
How Redact.dev Can Help Protect You
Staying safe on the web, and avoiding socially engineered attacks means securing your digital footprint. You can do this quickly and easily with Redact – the only platform in the world that lets you bulk delete content across all major platforms, with specific keyword filters.
With Redact, you can delete every post that mentions the college you went to, or the suburb you live in in just a few clicks.
We support a massive, growing list of social media platforms for bulk deletion. You can download Redact.dev for free and start securing your digital footprint across Facebook, Discord, Twitter and Reddit.