
Phrack Journalists Suspended from Proton Mail
Categories: Cybersecurity, Data Privacy, Data Safety, Digital Footprint, Policy, Social Media
Two Proton Mail accounts used by journalists working for cybersecurity publication Phrack were suspended after Proton received an alert from a cybersecurity response team. The accounts were later restored after a public outcry, but questions remain about the trigger, the appeals process, and how Proton evaluates these cases.
Phrack is a digital magazine written for and by hackers, widely circulated among hackers and computer security professionals, originally published in 1985.
What did the Phrack journalists do?
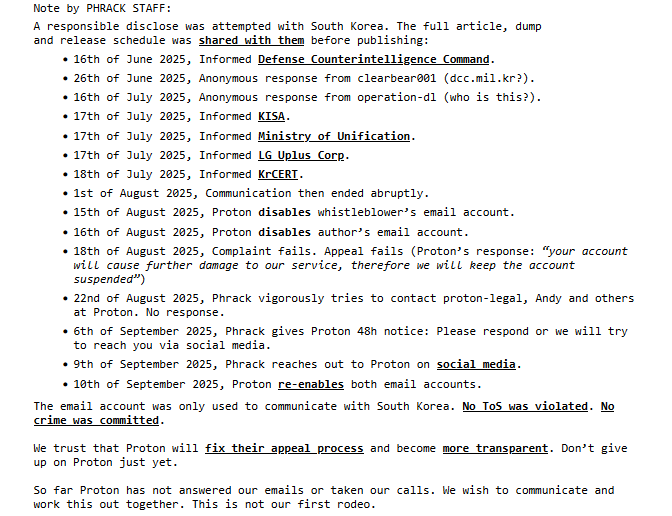
Phrack contributors created Proton Mail accounts while researching intrusions tied to a North Korea linked group. Reporting indicates the journalist’s Proton accounts were used for responsible disclosure to South Korean agencies. In mid-August the dedicated disclosure account was suspended, then one journalist’s personal Proton account was suspended the following day.
Phrack staff have documented the sequence of events diligently here. After necessary disclosures, Proton disabled both accounts. Proton rejected the whistleblower’s initial appeal, and for days, claiming “your account will cause further damage to our service, therefore we will keep the account suspected”.
Phrack repeatedly attempted to contact Proton with no response, for over a week – the full log of their efforts (and investigation are below).
Nearly a month later and after considerable effort, Phrack decided to reach out to Proton via social media (publicly);
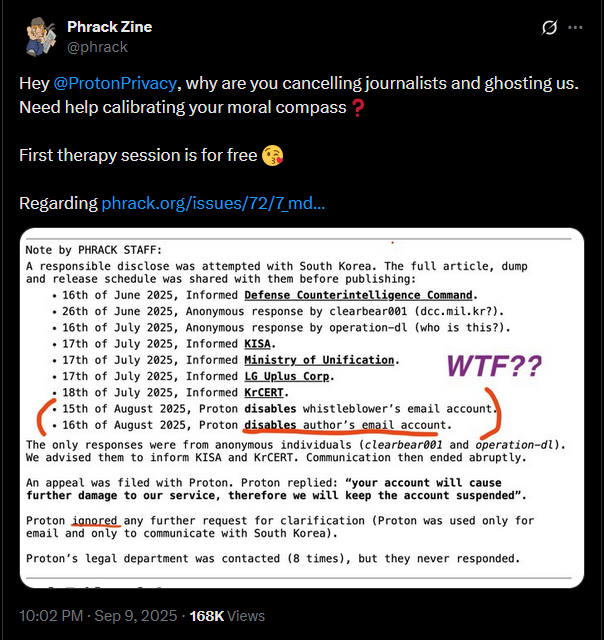
Why did Proton ignore Phrack’s Journalists?
Proton replied to the public call-out quickly, but despite their claim of “not ghosting”, Phrack did not receive any meaningful correspondence from Proton for the weeks their accounts spend suspended. Instead, they claim their unresponsiveness was due to a Computer Emergency Response Team (or CERT) alerting them to misused accounts.
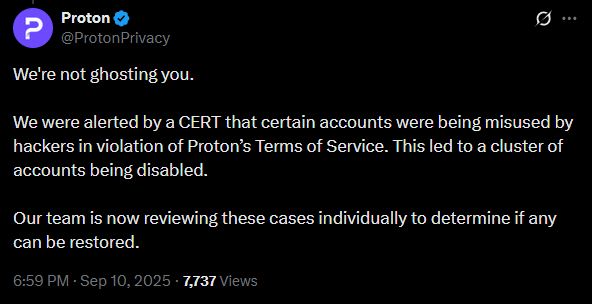
Proton said it had been alerted by a CERT that a cluster of accounts was being misused in violation of the Terms of Service. The company said cases would be reviewed individually, affirmed support for journalism, and noted that anti-abuse actions can affect legitimate users because Proton cannot see message content. The CEO also reiterated that hacking violates Proton’s ToS and is illegal in Switzerland.
What the journalists and editors say
The authors deny any hacking via Proton infrastructure and say the accounts were used to warn affected parties. Appeals were initially rejected and emails seeking clarification went unanswered for weeks. Phrack argues that the suspensions hindered reporting and disclosure work and asks Proton to publish the specific request that led to the action, along with a clearer appeals path.
Their response to Proton was also public. It has not received a public response, but it does appear constructive:

What are the consequences of mass suspensions by Proton?
After the incident drew wide attention, Proton restored two suspended accounts. Proton did not identify the CERT or explain the criteria used to suspend and then reinstate the accounts, leaving transparency questions open for reporters, researchers, and whistleblowers.
“Shoot first and ask questions later”, as Phrack put it, can compromise the privacy and security of end-users. For journalists, privacy and anonymity is often paramount for their safety. Suspending their Proton accounts may inhibit ongoing reporting, or force them onto other platforms.
If you’re a journalist, there are some practical steps you can (and should) take regardless of your use of Proton products.
Practical steps for journalists and researchers
Use this quick checklist to reduce disruption if a provider takes action on your account.
• Separate roles. Use distinct accounts for tips, disclosures, and publishing. Ideally, use options with E2E encryption.
• Maintain backups. Keep offline copies of contacts and crucial messages.
• Build redundancy. Prepare a second secure email or messaging channel and inform trusted contacts in advance.
• Document everything. Save suspension notices, appeal submissions, and ticket numbers for later review.
• Limit single points of failure. Avoid concentrating all disclosure work in one mailbox.
Open questions that still need answers
These details would help high risk users plan and assess provider safeguards.
• Which CERT sent the alert to Proton, and what evidence triggered it.
• What criteria Proton uses to suspend clusters of accounts and how appeals are evaluated.
• How Proton balances ToS enforcement with its stated mission to protect journalism and whistleblowing.
Reduce what others can use against you
Platform decisions are not always predictable, but your public footprint is. Redact helps you cut risk by shrinking the data trail that fuels false flags, profiling, and pile-ons. For journalist’s specifically, our local archive feature can save local copies of your conversations, posts, comments, emails and more (if you enable it).
Redact supports dozens of major social and productivity platforms. Bulk delete old posts, comments, likes, and messages across major networks. Filter by keywords or dates, preview changes, and schedule recurring cleanups so you stay ahead of problems. Keep your footprint small and your focus on the work that matters.
You can try it free for deletions on Discord, Twitter, and Facebook, and mass-edits on Reddit.