A New Era of Digital Security: What Apple’s PQ3 Encryption Means for You
Categories: AI, Cybersecurity, Data, Data Privacy
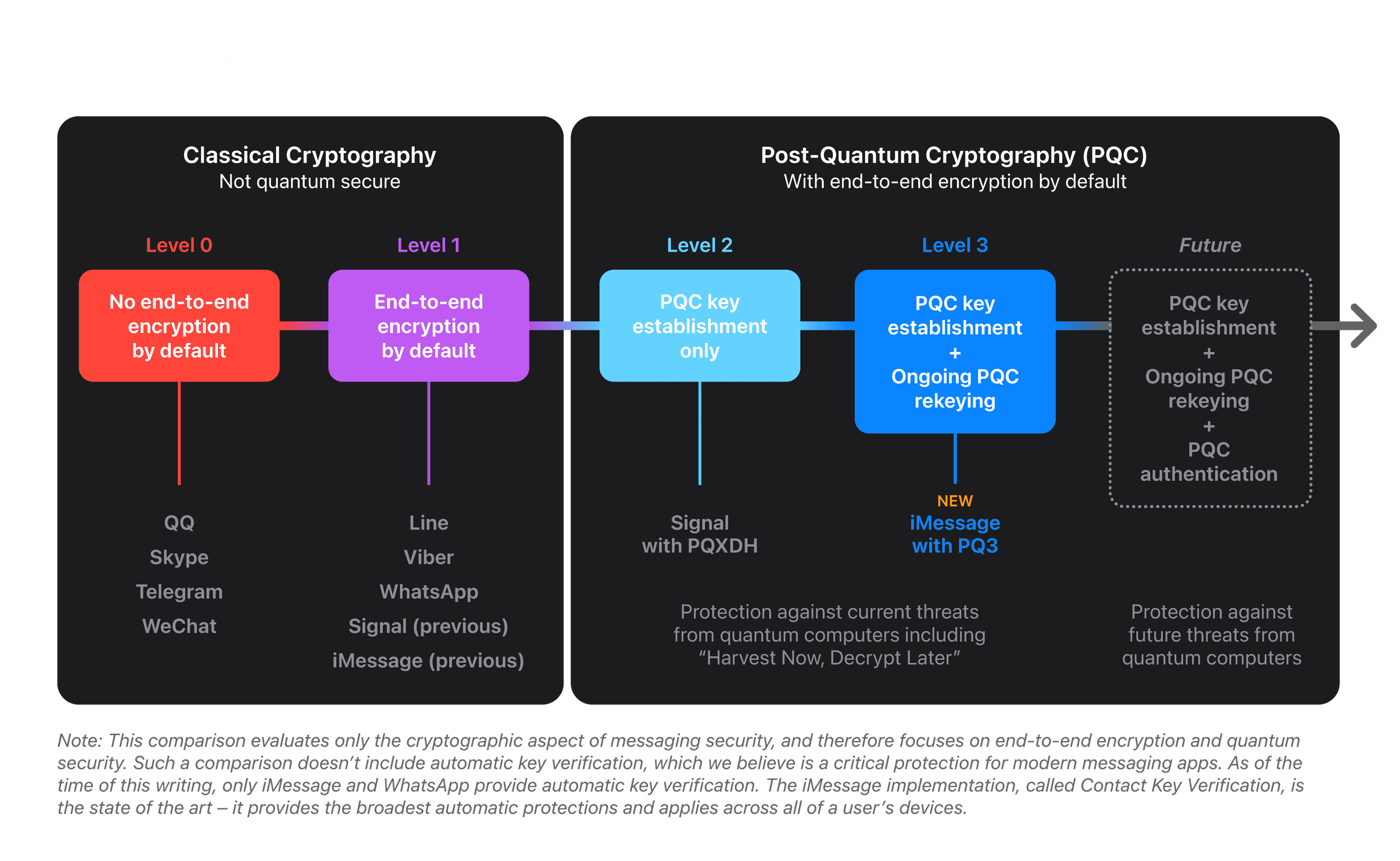
Apple’s release of iOS 17.4 brought with it a groundbreaking feature in cybersecurity: PQ3 encryption for iMessage. This advanced security protocol is designed to protect sensitive data from threats posed by quantum computing—a technology poised to reshape the landscape of cybersecurity. But what does this mean for you, and why should you care?
Let’s break it down.
The Basics of PQ3 Encryption
Imagine a world where today’s strongest locks can be picked in seconds. That’s the threat posed by quantum computers to traditional encryption methods. Apple’s PQ3 encryption—short for Post-Quantum Cryptography Level 3—is the company’s answer to this challenge.
Using a blend of advanced algorithms like KYBER (a lattice-based cryptography method) and Elliptic Curve Cryptography (ECC), PQ3 creates a robust shield against current and future cyber threats. Unlike older methods such as the Caesar cryptography or even modern standards like the Advanced Encryption Standard (AES), PQ3 is specifically designed to withstand the unique challenges posed by quantum computing. Its purpose? To safeguard your data from a hacking tactic called “Harvest Now, Decrypt Later” (HNDL), where attackers store encrypted data today, waiting to crack it once quantum computing matures.
Why Now?
While quantum computing is still emerging, its potential to disrupt digital security is enormous. Tools like ProtonMail and BitLocker are already leveraging advanced encryption to protect data, showcasing how innovation in cybersecurity is critical to staying ahead of these threats. Today’s encryption methods—like RSA 2048, which could take traditional computers billions of years (or longer) to crack—would stand no chance against quantum machines. By adopting PQ3 encryption, Apple is staying ahead of the curve, ensuring that your personal and professional data remains secure for years to come.
How Does PQ3 Work?
Apple’s PQ3 isn’t just a theoretical improvement; it introduces tangible security enhancements. One standout feature is key rotation, where encryption keys automatically change after every 50 messages or seven days. This limits the damage a compromised key can cause, making it nearly impossible for hackers to unlock entire data streams.
For users, this means a significant boost in the security of their iMessage communications, now securely cyphered to protect against evolving cyber threats.
What It Means for You
For the average user, PQ3 encryption represents peace of mind. Your personal communications which may include financial data and private files will be better protected from both current and future cyber threats under PQ3. But as technology advances, so do the methods used by cybercriminals – which we wrote about recently. That’s why managing your digital footprint has never been more important.
Even with Apple’s advanced encryption, the sheer volume of information people share online increases the risk of data breaches – though iMessage is considerably less vulnerable with PQ3 implemented. Tools like Redact.dev can help you reduce this risk by enabling you to delete old posts, messages, and other digital traces across various platforms. It’s a simple but powerful way to complement robust encryption like PQ3.
Why Managing Your Digital Footprint Matters
Think of your online presence as a digital diary. While some entries may seem harmless, others could expose you to risks like identity theft or social engineering attacks. Pairing Apple’s PQ3 encryption with tools like Redact.dev ensures your data is not only secure but also minimized to reduce vulnerabilities.
By proactively managing your digital footprint, you’re taking a two-pronged approach to digital security: protecting sensitive information with encryption, which far surpasses simpler methods like Caesar crypto, and reducing unnecessary exposure.
The Future of Digital Security
Apple’s PQ3 encryption marks a turning point in the fight against cyber threats. As quantum computing continues to advance, businesses and individuals must stay vigilant. The best time to bolster your digital defenses is now.
Here’s how you can start:
- Use encrypted platforms: Opt for services that prioritize security, like those implementing PQ3 encryption.
- Rotate your passwords and keys: Regular updates make it harder for hackers to exploit vulnerabilities.
- Manage your digital footprint: Leverage tools like Redact.dev to clean up old data and stay ahead of potential breaches.
The digital world is evolving, and so should your approach to security. With Apple’s PQ3 encryption and proactive steps like reducing your online footprint, you’re better equipped to navigate the future safely.