How to Prevent Doxxing: A 24-Hour Privacy Sprint
Categories: Cybersecurity, Data, Data Brokers, Data Privacy, Digital Footprint, PII, Privacy Guides
Anyone can get doxxed – and the consequences can be huge. It can impact your personal relationships, career, and future prospects. Lets understand what it is, how you can prevent it, and the actionable steps you can take today.
What is doxxing?
Doxxing is the intentional act of de-anonymizing someone’s online identity, personal info, or details without consent. Doxxing is deliberate, and done with intent to cause harm. For example, the recent Tea App breach involved internet users deliberately harvesting data about thousands of Tea users, and publishing it with the intent to cause harm; in this case, the Tea App didn’t dox anyone (though there were negligent), but the individuals that acquired and published the data did dox Tea users.
How can you avoid getting doxxed?
While doxxing can occur through a variety of unethical techniques, preventing it from happening to you is relatively simple – shrink the amount of personal data a bad actor can use.
We’ve built a 24-hour sprint plan that you can follow to reduce the risk of getting doxxed without nuking your entire digital footprint. This plan focuses on rapid, user-controlled changes that you can do for free, and optional batch cleanups with the Redact App to keep your privacy even more secure.
Important
If you face an active threat, contact local authorities first. Preserve evidence before you remove or edit anything.
What you will need
- Account access for your major platforms
- Redact installed to run previews and batch actions (recommended)
- One hour of quiet focus to start, then short blocks through the day(s) until complete
Sprint plan at a glance
- 0 to 1 hour: lock down privacy and pause exposure
- 1 to 2 hours: passwords, recovery options, and 2FA
- 2 to 4 hours: batch delete with rules and previews
- 4 to 6 hours: images, video, and location data
- 6 to 8 hours: platform specific privacy passes
- 8 to 12 hours: search yourself and fix stray exposures
- 12 to 16 hours: people finder opt outs and domain hygiene
- 16 to 22 hours: device, network, and social graph hardening
- 22 to 24 hours: final audit and a recurring schedule
0 to 1 hour: immediate exposure freeze
The first thing you should do is freeze as many exposure points as possible;
- Set every social profile to private or friends only where possible
- Turn off public tagging and limit who can mention you
- Hide phone number, email, birthday, hometown, schools, employer
- Disable location sharing in apps and remove live location in chats
- Remove public friend lists and follower lists where a platform allows it so your attacker can’t target your friends and family
1 to 2 hours: access security
After freezing exposure points, you need to ensure your security settings across all accounts are up-to-par. That means passwords, 2-factor authentication, recovery emails/phones on all platforms + a quick review of active sessions.
- Change passwords on email, social, cloud storage, and your password manager. Ensure they’re all complex and unique. Use a mix of symbols, numbers, letters, and aim for long, unique passwords on all accounts.
- Add 2FA everywhere, ideally using an authentication app or passkeys rather than SMS or email authentication.
- Check recovery email and phone on all accounts. Make sure you remove old or shared recovery methods.
- Review active sessions and log out devices you do not recognize. If you notice unrecognized devices – make sure you update your password and set up multi-factor authentication.
2 to 4 hours: review your public and private content
The next step involves reviewing public and private content on your social media accounts – specifically searching for any information that could be used to profile you. We’ve included a few critical ones below.
- Phone numbers
- Email addresses
- Current & former addresses (we recommend avoiding any level of location data – even just the city)
- School/workplace (better to keep them off the internet if you can)
- SSN, mother’s maiden name, images of documents
- Full names of your close family, friends etc.
If you’re doing this manually, you’ll need to go through each social media profile and search for these traces of personal information. Depending on how much history you have online, this may take even longer than 4 hours. That’s why we built Redact.dev – the only social media deletion tool that covers almost every major social media platform; Discord, Reddit, Facebook, Twitter, and ~30+ others.
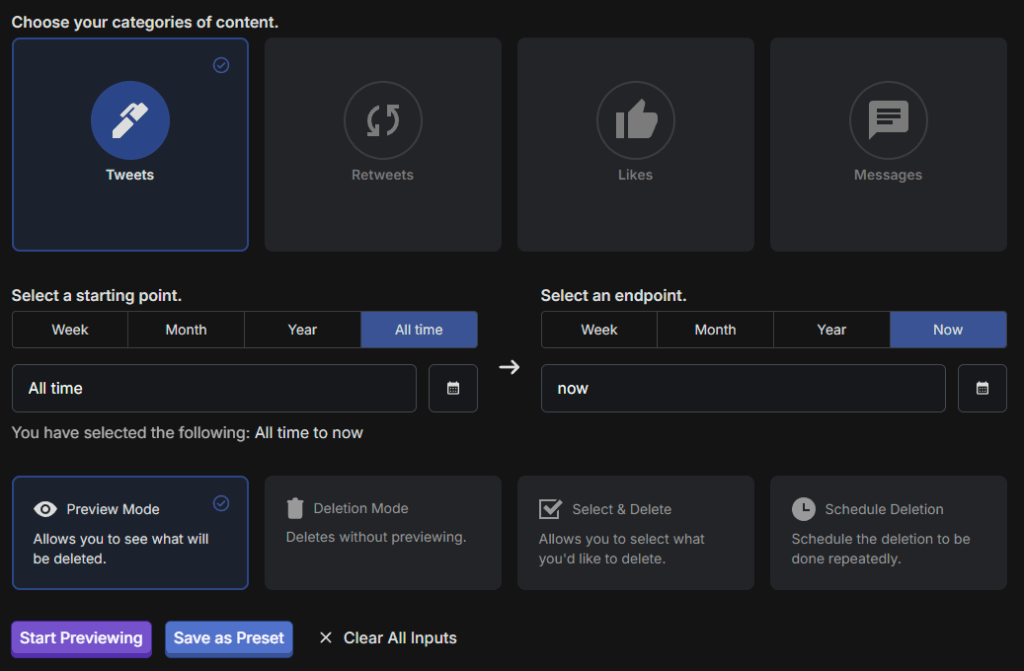
If you’re using Redact, you can use the list of data types above and our keyword filters (in the Advanced form) to locate content with specific words, phrases, or numbers. Then, run a Preview Mode job to see the results. If you’re happy deleting what you see, return to the form and re-run the setup using Deletion Mode.
Target your search across posts, comments, bios, replies, captions, and reactions. Always preview before you delete, or use Select & delete for an efficient, bespoke review.
4 to 6 hours: images and metadata
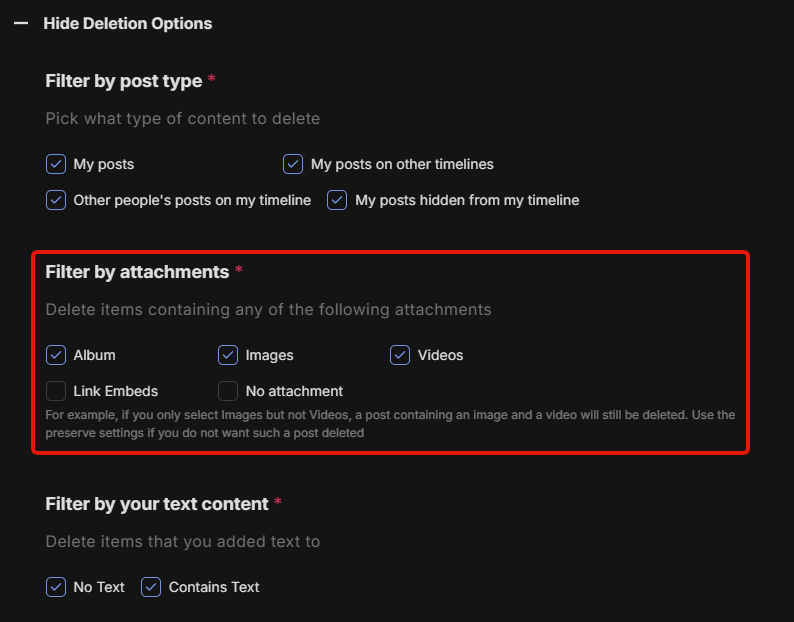
After the sensitive text has been cleaned up, you need to do the same thing for images and metadata. That means reviewing your profiles & image/video posts, and removing any that show;
- Addresses
- Street signs
- Unique yard details
- Mailbox names
- Work ID badges
- Vehicle plates
- Boarding passes, barcodes, QR codes
You can always save the content, scrub the sensitive element, and re-upload it if you want.
If you want to speed this process up even more, use Redact.dev. You can scan almost any social media platform for images, albums, videos and other content types. Using Preview or Select & Delete mode, you’re able to easily review everything on one page, locate the risky content, and delete it.
6 to 8 hours: platform passes
Once you’ve reviewed and resolved content and login based vulnerabilities, it’s time to get your public data under control. Specifically, review all your social media platforms engagement settings and set the strictest controls for;
- Who can tag you, message you, and see your followers
- Hide or remove old bios that list city, job, or school (Facebook in particular will often post ‘life events’ when you move, or your relationship status changes)
- Remove old likes and comments that may reveal routines or places (you can use Redact.dev for this too)
- Leave or hide from public groups – especially if they expose location or employer.
8 to 12 hours: search yourself like an attacker
Now that you’ve got the basics covered – it’s time to go a level deeper. You need to approach your own digital footprint as if you were an attacker.
Here’s how to get started –
- Search your full name, usernames, common misspellings, and old handles
- Check images search with your selfies and profile photos (use a reverse-image search tool)
- Look for old public folders, paste sites, public boards, old classifieds that mention you
- Find and fix stray exposure points. Make private, remove, or rename.
If you want to go even deeper – check out OSINT Techniques Recommended Tools, and OSINT Framework.
12 to 16 hours: people finder and domain hygiene
You’re nearly done! The next steps are about removing data about you on the web that you don’t own (data brokers), and if you have a website – ensuring it’s set up securely & in a privacy-conscious way.
- Start opt outs on major people directories. Expect removal to take weeks. Here’s a list of the “best” ones you can start with.
- If you own a domain, enable privacy on WHOIS – google “enable WHOIS privacy [your_domain_provider_here]”
- Remove public contact pages from your website/s that list any personal details.
- Clean public any repos and gists that include personal data
16 to 22 hours: device, network, and social graph hardening
If you’ve made it this far, you’re probably more secure than 99% of folks on the internet. Regardless, you can go even further.
- Rename devices so they do not contain your full name
- Update your router name and remove home address from network labels
- Remove old Wi-Fi networks and Bluetooth pairings
- Prune your followers and friend lists. Remove unknowns, set lists to private
- Ask close contacts not to tag you or share your location
22 to 24 hours: final audit and schedule
At this point, you’re basically done. Once you reach the final hours, we recommend re-running a few critical steps to ensure your earlier actions worked (and didn’t miss anything).
- Re run your search terms and spot check a few platforms
- Keep a private log of what you changed and when
Finally, set a calendar reminder to re-run this guide every 1-3 months. If you’re using Redact.dev, you can automate social media cleanups on major platforms to keep your dox-risk as low as possible.
When not to delete
You might be thinking “this guide is going to make me delete all most content” – and really, you should delete as much as you can. However, there are a few important exceptions;
- If a post or message is evidence of harassment or a crime, preserve it first with full headers and timestamps
- If an employer or court has a legal hold, follow that policy
Minimal checklist for a friend or partner
If you’re concerned someone in your network (friends, family or even colleague) might share sensitive information without realizing – it might be worth talking to them about the risk of having exposed information online. Additionally, you should consider talking to them about;
- Not tagging or mentioning you in public content
- Never using your full name, location, or sharing photos of you
- Ensure groups or group chats are set to private
- Asking before posting anything that uses your name, voice, image, or info about you
While this can be awkward, if you’re able to help others understand the risks, and take healthy preventative measures it will reduce their risk – and yours!